One if top ransomware groups!
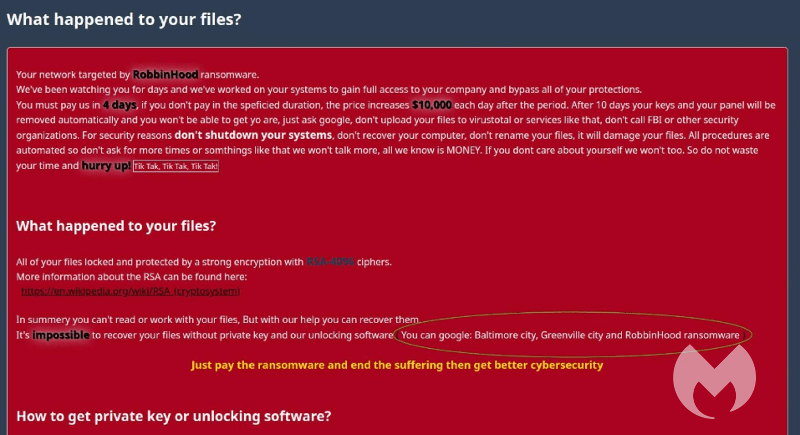
RobbinHood is one of the most wanted entities is the space of ransomware, followed by Locky, Cerber, Maze, WannaCry, Ryuk groups. While most of them target individuals, RobbinHood attacks large networks, both corporate and government. As this garners lump sums rather than pennies. The attacks they do are of simple known methods, and the ransomware they ask ranges on the size of the network. This could be from 3 Bitcoins (for a single computer) to 13 Bitcoins for an entire network. Nevertheless, this sum could be entirely depending on the party, sensitiveness of encrypted data and size of the network. In Baltimore’s case, the city has paid RobbinHood a sum of 13 Bitcoin ($80,000) to retrieve their network but had to patch all the vulnerabilities which cost them more than $10 million. RobbinHood, as a part of its operation to gain internal access, shall exploit the Remote Desktop Protocol (RDP) of systems by brute force attacks or by dumping trojans by phishing emails. This would let them exploit a vulnerable kernel driver of Gigabyte motherboards, which isn’t flagged by any softwares as Windows accepts it as a legitimate entrant, by verifying Gigabyte’s signature. This access can help an attacker to stop various services as antivirus softwares, disabling backup, deletion of files, clearing event logs etc. And when set with all this, it starts encrypting the files and renames them as Encrypted_[randomstring].enc_robbinhood Further, it leaves C: disk files to make the system work at least and let victim find their ransom note.
Avoiding RobbinHood, or in this case, any such attacks could be simple. Having effective IT teams in every organization should avoid most of the problems, as they should be monitoring of communications happening over RDP, and blocking any unused ports. Further, applying the latest patches from providers and having the best antivirus softwares could help avoid such attacks. Source – MalwareBytes